What is Network Access Control (NAC)?
Cybersecurity is one of the rising concerns in the digital world, which needs to be tackled from various perspectives.
Though digitization offers more improved efficiency, flexibility, and optimization, it is inherently untrustworthy.
It is important to control and manage access to the network and with the increasing complexity of IoT, it is becoming an extremely different task.
Currently, many companies have antimalware, firewalls, and dozens of other software to fight off this threat.
But along the line, a more dynamic, automated, and centralized option is needed to tackle the problem.

What is Payment Switch - Working, Architecture, Features, and Benefits
What is Payment Switch - Working, Architecture, Features, and Benefits Simply said, Payment Switch is a tool that facilitates communication...
This is where NAC comes into the picture
NAC, abbreviated from Network Access Control is exactly what the name says. It is a server/software which controls access to your network.
It integrates with the wired and wireless infrastructure and identifies, assigns, and enforces pre-determined rules to manage access to the network.
Why NAC is important?
NAC can be considered a foundational block of the security network. It is a highly secure and powerful network server for security defense.
Based on Authorization, Authentication, and Accounting, NAC provides network visibility and monitors network devices, and provides next-generation security measures, protocols, and end-point security.
NAC is designed to handle large enterprises’ networks that have all-time connecting devices. It has a set of predetermined rules or protocols, which helps to block the attack before it comes.
NAC is responsible for storing and applying the company’s access protocols and distributing them depending on the devices that want to access the network and its request.
NAC works on 2A’s that is, authentication and authorization
Authentication: NAC verifies the identity of the user/device that is trying to access the network. This is done by entering credentials, username/password, or by biometric.
Authorization: Once the authentication is done successfully, NAC goes through the predefined policies and protocols to check whether the device/user should be approved or not.
General Steps to Implement NAC Solutions:
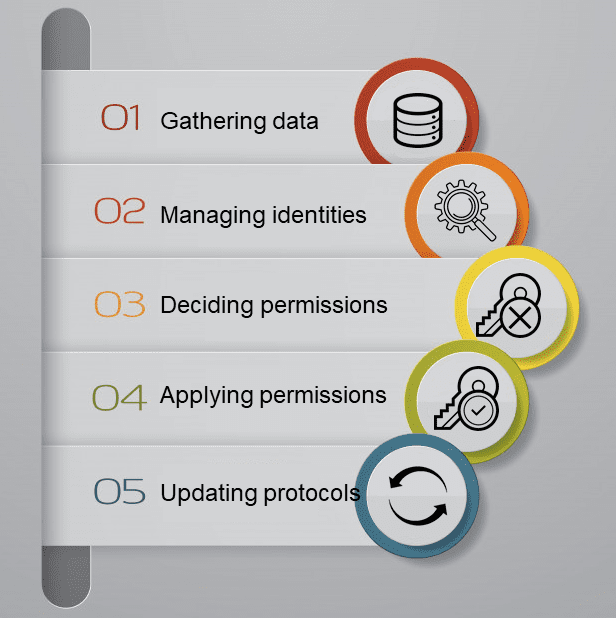
- Gathering data from every device and server
- Managing identities based on protocols
- Deciding permissions
- Applying for permissions
- Updating protocols
NAC capabilities: (Main functions of NAC)
The main goal of NAC is to maintain, manage and defend the entire network of an organization. The entities covered in the whole network are physical, wired, wireless, and cloud-based infrastructures.
NAC allows the identification of what or who is accessing your network and what path they are going through.
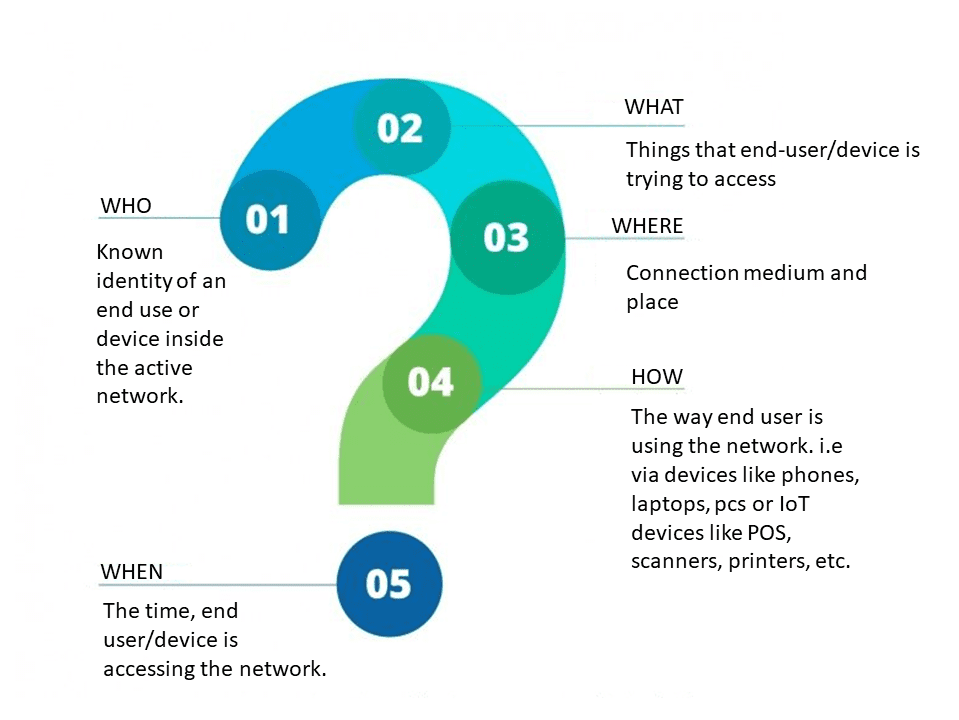
- Who is the end-user and are they a known user inside of your active directory?
- What is the end-user or device (IoT) trying to access on your network?
- Where are they connecting to the wifi? In their office, the cafeteria, hotel room, dorms…etc.
- When are your end-users or IoT devices accessing the network? Knowing this will also give you insights into when they are most active and least active, helping you to distribute bandwidth more efficiently.
- How your end-users are accessing your network (smartphones, laptops, tablets) as well as what IoT devices/systems are accessing your network (security cameras, vending machines, HVAC, scanners, printers, POS systems, etc.)
After identifying what or/and who is trying to access the network, NAC assigns proper roles to the device/user trying to access the network.
As said previously, NAC has a set of predetermined sets of rules and it has role-based access control with which the right type of network experience can be customized based on the type of user/device. These rules provide users and devices the access they need by creating accurate protocols.
By controlling the behavior of all the devices/users that are trying to access the network, it provides endpoint security.

How 3DS payment gateway has affected Ecommerce industry in India
3DS (3 Domain Secure) forms one of the most innovative births in the family of online payments. The protocol developed by VISA to improve online...
Listing down the main capabilities of NAC:
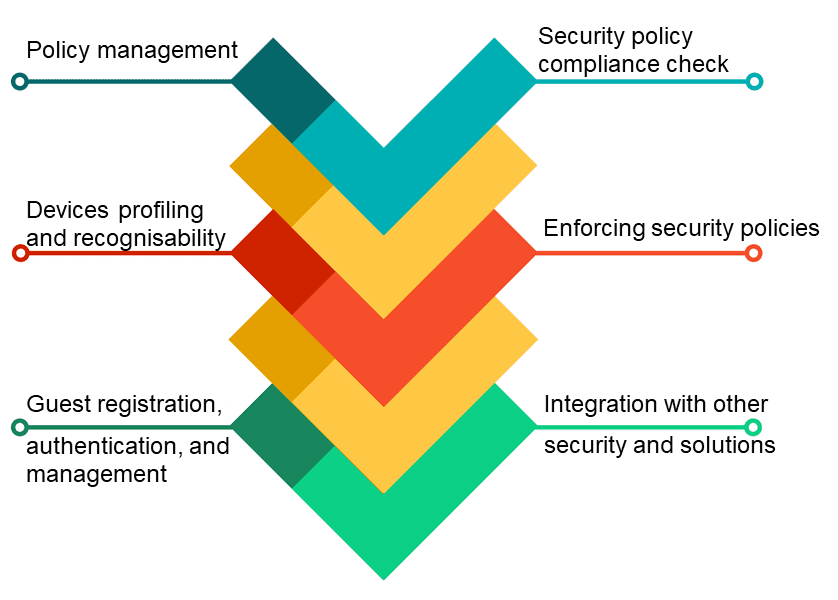
- Policy lifecycle management: Enforces policies for all operating scenarios without requiring separate products or additional modules.
- Profiling and visibility: Recognizes and profiles users and their devices before malicious code can cause damage.
- Guest networking access: Manage guests through a customizable, self-service portal that includes guest registration, guest authentication, guest sponsoring, and a guest management portal.
- Security posture check: Evaluates security-policy compliance by user type, device type, and operating system.
- Incidence response: Mitigates network threats by enforcing security policies that block, isolate, and repair noncompliant machines without administrator attention.
- Bidirectional integration: Integrate with other security and network solutions through the open/RESTful API.
Some examples of NAC for various sectors/industries
- NAC for partners, employees, or guests: Every business, at some point, is dependent on some third-party partners, they may be contractors, vendors, or some other visitors depending on the industry field. It is important to share the necessary data with these third parties. NAC differentiates access from employees and non-employees.
- NAC for BYOD: BYOD or Buy Your Own Device is currently in trending. Evolved technologies and the introduction of IoT have given employees the freedom to work remotely. As there is no control over employees’ devices, this makes a difficult task for IT and security. In such cases, NAC makes sure of the compliance of employees’ devices before accessing the network.
- NAC for IoT: Irrespective of industry, the usability of IoT devices is increasing very rapidly. Usually, BYOD devices use a common operating system, which is why they are easy to control. This is a little difficult considering IoT devices may not have common operating systems. NAC reduces the risk by applying defined protocols and access policies depending on device categories.



